
Photo by FKS
Cybersecurity and the like
This year’s “FKS connect IT!” one-day conference will take place on 07 September 2023. In the very nice ambience Yu Garden Hamburg experts and interested parties from the security sector met. Here is the agenda:
Christian Schröder (FKS)
Opening of FKS connect IT! 2023 by the FKS management
Volker Kozok, Cybersecurity Expert
Nothing new in the West, Russian cyberwar and the impact on politics and business
Stefan Fritz, Senior Manager Channel Sales (Sophos)
Cybersecurity as a service - sense or nonsense?
Olaf Schindler, Senior Channel Account Manager DACH (Forcepoint)
Quo vadis IT security - Where is the market heading?
Andreas (Andi) Kaßler (SARK Solutions)
David Berger, Enterprise Account Manager (Pentera)
Sometimes you're just too late ... and what you can do about it
Jan Bräuer, Authorised Signatory (FKS)
How, what, when and where? Orientation and planning in an uncertain & complex IT world: information security made simple.
Oliver Listl, Senior System Engineer (Infinigate)
At some point it hits EVERYONE
Patrick Böhm, Team Leader Micosoft (FKS)
Tim Themann, Head of Professional Services (FKS)
consulting.365 - Structured for more security and resilience with Microsoft 365
Gabriel Zajusch, Sales Managed Services (FKS)
Tede Mertens, System Engineer (Veeam)
Ultra-Resilient Backup in the Hamburg Cloud
Heinz Mäurer, HP Wolf Security (HP Germany)
Time for a different Endpoint Security?
A small selection of topics
Overall, the conference was a great event. Impressive is the fact that FKS organised and implemented everything themselves. That means the moderation, sound, audio, speaker support, online stream … . Really great. And the food was also very good, despite the subtropical heat in the garden.
Quo vadis IT-Security - Where is the market heading?
I liked the presentation by Olaf Schindler (Forcepoint), because Olaf first dealt with the topic of Generative AI in general. Here is a good statement by Dr. Souhir Be Souissi:
There are virtually no limitations on how these systems can be combined with other technologies, especially with other, more classical forms of software. The output they (AI) produce, either in the form of text, code or images, can easily be used by other subsystems to form a general solution.
He also shed light on the concept of enshittification. This comes from Cory Doctorow and it deals with the deterioration of the usefulness of online platforms which he defines as a degradation of an online environment caused by greed:
Platforms die as follows: First they are good to their users; then they abuse their users to make things better for their business customers; finally they abuse those business customers to get all the value back for themselves. Then they die. I call this “enshittification”, and it is a seemingly inevitable consequence that results from the combination of the ease with which a platform changes the allocation of value, combined with the nature of a “two-sided market” in which a platform sits between buyers and sellers, holding each hostage to the other and grabbing an ever-increasing share of the value that is conveyed between them.
Source: https://en.wikipedia.org/wiki/Cory_Doctorow
Finally, he introduced the Forcepoint SASE - Secure Acces Service Edge concept, This is composed of Forrester’s SSE (Security Service Edge) models and Gartner’s SD-WAN model:
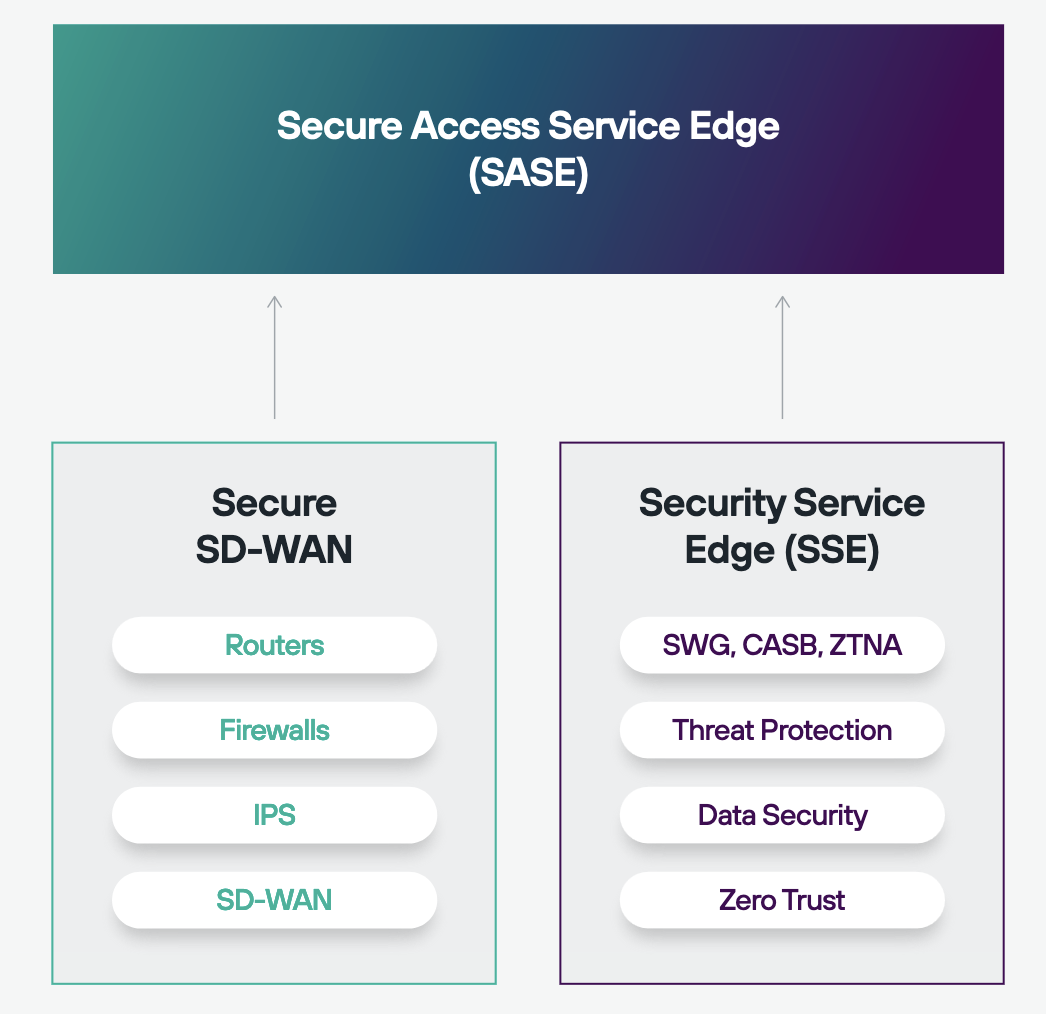
Source: The Practical Executive’s Guide to SASE - Whitepaper
He describes the goal as, “Empower your staff to take advantage of the latest innovations while protecting data.”
Sometimes you’re just too late … and what to do about it
I’ve become a big fan of Pentera as a tool, for continuously monitoring infrastructure for attack vectors. Pentera is not a protection tool. Pentera is the hacker. And that’s the only reasonable way to find out if my systems are hackable.

David Berger and Andi Kaßler presented Pentera live and impressively showed what the tool can do. Every company should use Pentera and find out where the weak points in their infrastructure are. Sark Solutions offers a first introduction and insight into the possibilities.
The key messages about Pentera are as follows:
- Most vulnerabilities that are exploited are more than two to three years old.
- Pentesting once a year or month is useless as attack vectors in the enterprise change daily.
- 3 points of Pentera:
- all data stays in the enterprise
- everything on premis
- no employee necessary because completely automated
- What you need to start: an IP address on the internal network
Ultra-Resilient Backup in the Hamburg Cloud
An equally good presentation came from Gabriel Zajusch (FKS) and Tede Mertens (Veema) on the topic of backup in the Hamburg Cloud (FKS). In doing so, they presented the “Data Protection Postcode 32110”. Here in brief:
3
3 Copies of the data
- Productive data
- Backup
- Backup copy in a co-location (tape, VCSP, cloud).
Analogue:
- CDP replication
- Snapshot
- Snapshot copy
2
2 different media
-
- disc
-
- tape
1
1 offsite copy
1
Offline, air-gapped, immutable or insider protected
0
No errors after checking backups for recoverability
The term ultra-resilience is explained like this:
- Insider Protection
- Protection against destruction of backups by moving them to the “recycle bin”.
- Restore to the cloud
- Secure data centre
- Separation of administrative responsibilities
Time for a different Endpoint Security?
Heinz Mäurer (HP Wolf Security) gave the last, but no less good, talk on the topic of attacks via hardware and people - e.g. a laptop and its user. Here is a claim:
Inherent risk
The interface between man and machine remains the number one entry point - more than 85% of all attacks start with the human factor. Because: Employees can always be attacked in a similar way, even when using the most diverse tools - via emotional manipulation and social engineering (social hacking).
Furthermore, he notes that “new targets, old targets are being rediscovered”:
- Attacks below the operating system
- Devices with remote access more in focus
- Printers
- Human factor
Significant and weighty here are the figures that in 2022 203 billion euros in damage were caused by cyber attacks in Germany. By comparison, federal tax revenues amounted to EUR 328 billion in 2022. Forecasts show that spending of EUR 6.9 billion on4 cybersecurity will continue to rise in 2022.
Conclusion
Cybercrime, cyberattacks, cyberwar and cybersecurity. It concerns all of us. We are not only talking about massive financial damage, but also reputational and emotional damage. It is therefore important to stay close to the solutions and not to shy away from taking costly and possibly uncomfortable paths. In business, but also increasingly in private life.